We’ve all heard talk of phishing scams and social engineering attacks—devious new ways for hackers to get access to our personal information. But what are they exactly? What is a phishing scam?
Understanding and Protecting Against Phishing Scams
Phishing is the process of attempting to acquire sensitive personal information (usernames, passwords, credit card details) by pretending to be a trustworthy entity. This is generally done using bulk email blasts that try to avoid spam filters.
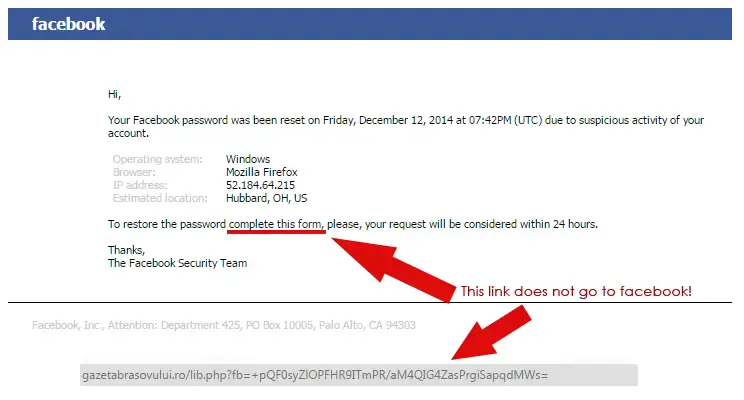
These emails can look like they’re from Facebook, Twitter, LinkedIn, and ask you for a password reset—which would also require your username. Just like that, the hacker has access to your account, which includes all of your personal data: your home address, your workplace (where they now know they have an easy target: you), and even your personal likes or dislikes. This lets them further target you and your connections for other kinds of scams.
Even more nefarious is when phishing scams pose as a more influential organization: your bank, for example. The email could have a subject line that reads, “Unauthorized Account Access: Immediate Action Required” and asks you for your username, password, PIN, and account number.
Within twenty minutes, you’ve been robbed and locked out of your own account. Similar attacks could also ask for your social security number, which opens the door for identity theft—a life-destroying crime.
When you receive a phishing email, few people would blame you for being tricked. These emails will often have the exact presentation of an official email from that source, down to the signatures and layout. The link they provide will drop you on a website that also looks entirely legitimate, to further make you feel safe in divulging your data.
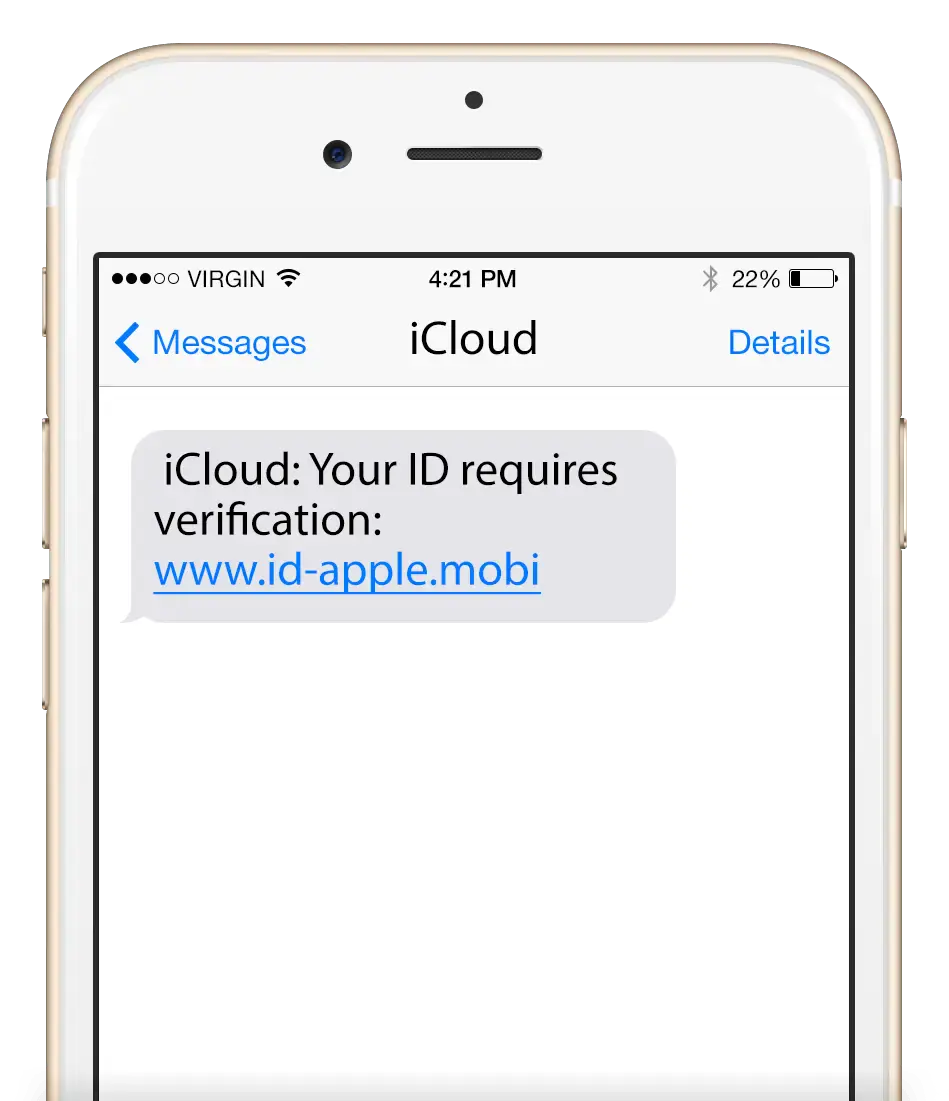
When 90% of successful hacks and data breaches start with phishing scams, it’s obvious that anyone can be fooled. These attacks come in more than just email; they can come in the form of voice phishing, where a similar trick is attempted via a phone call, or SMS phishing, where it’s done via text (especially as more companies are utilizing some form of text-line service). Various forms of malware and ransomware can also lead to the same result.
So how do you protect yourself from phishing?
There are a few easy solutions, and the most basic is to think before you click.
If you know you haven’t requested a password reset for any of your accounts, you should be suspicious if one comes in. Another easy adaptation (one that helps protect you from a variety of hacking attempts) is to enable multi-factor authentication on your accounts; things like text confirmation or some kind of fingerprint scan.
When it comes to specifically email phishing, hover over/click the email address of the email to see if the domain looks legitimate. It’s especially easy when you can compare the suspicious email’s address to the real thing.
If it doesn’t match up, don’t interact with it any further.
To ensure no one in your organization falls victim to a phishing attack; you should really work with a Technology Expert to develop a documented security policy and share it with your team. Once the policy is developed and shared, regular training should be scheduled to ensure that the policy is adhered to on a regular basis.
Anyone can be victimized by a phishing attack. Our job at Attentus is to help you learn about the threats, and give you the tools to defend against them.
Give us a call if you’re interested in a robust and reliable IT resource that can help you navigate the muddy waters of modern IT security.
