They look great on paper, but why do so many cyber security plans fail? Without a well-formulated cyber security implementation plan, 2 out of 3 CIOs doubt their organization’s security readiness.
In this blog, we’ll help you understand what a cyber security implementation plan is and guide you step-by-step through implementing a security plan in your business. This way, you can become the 1 out of 3 and be miles ahead of your competitors.
What is a Cyber Security Implementation Plan?
A cyber security implementation plan is a strategic roadmap that outlines the measures you should take to safeguard your digital assets, networks, and systems from cyber threats.
It identifies the potential risks, outlines the necessary controls and processes, and assigns roles and responsibilities to employees. This plan is crucial for your business to protect its valuable data and ensure continuity in the face of ever-evolving cyber threats.
Maximize effectiveness while streamlining systems with a team that supports unique needs across industries
Our Clients
8 Steps for Implementing a Cyber Security Plan at Your Business
Step 1: Build a Checklist
A well-defined cybersecurity policy serves as the foundation of your cybersecurity strategy. However, realizing it in the real world requires a step-by-step approach. Start by developing a checklist with the big and little things that you need to accomplish. Your checklist should:
- Provide clear goals for your team
- Outline KPIs to measure the success of the efforts
- Identify mission-critical IT systems
- List out key activities, such as patching
- Identify people responsible for each action item
Preparing a checklist makes it much easier to allocate tasks amongst your team, and allows you to verify if they have been completed as intended.
Step 2: Assess Your Current Cybersecurity Posture
This involves taking stock of your IT infrastructure, hardware, software, network, and data storage systems. Perform a risk assessment to understand which aspects need immediate attention and allocate resources accordingly in your cybersecurity implementation plan.
Prioritize mission-critical areas of your IT infrastructure, such as the business network and data storage.
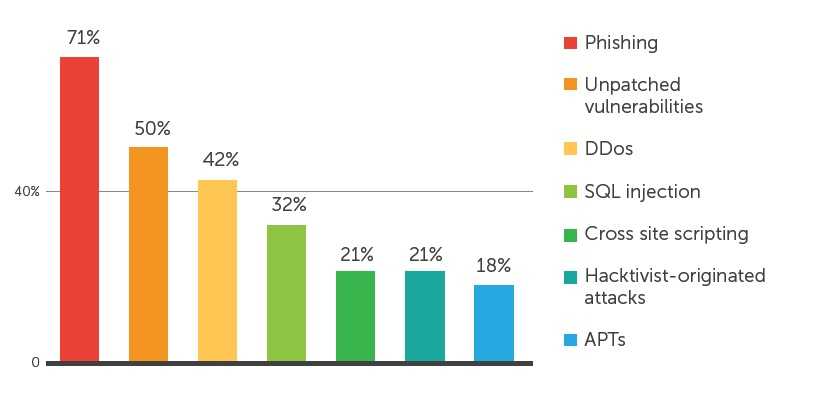
Caption: Most common attack vectors; CIPSEC
Step 3: Define Your Cybersecurity Goals
With a clear understanding of your current cybersecurity state, it’s time to define your goals. These goals will guide your strategy and help you prioritize which areas to focus on. Some common goals include:
- Protecting sensitive data
- Ensuring business continuity in the face of cyber threats
- Compliance with industry regulations and standards
- Building customer trust and confidence in your organization’s security
Defining KPIs for each of these goals is vital for measuring the success and effectiveness of your security. One such measure can be assigning suppliers you work with a letter grade for the cybersecurity measures they have taken. For your own organization, utilize ones such as Mean Time To Detect (MTTD), to ensure your own readiness.
Step 4: Establish a Cybersecurity Team
Establishing a dedicated cybersecurity team is crucial for implementing and maintaining your cybersecurity program. This team can consist of in-house IT staff or outsourced cybersecurity professionals, depending on your organization’s size and needs.
Assign specific roles and responsibilities to ensure everyone is aware of their part in maintaining and enhancing your organization’s security posture.
Step 5: Implement Security Controls
With your policy in place, the next step is to implement the necessary security controls. These controls should be tailored to your organization’s specific needs and risks. Some examples of security controls include:
- Regular software updates and patches
- Firewalls and intrusion detection systems
- Encryption of sensitive data
- Strong password policies and multi-factor authentication
- Regular security audits and vulnerability assessments
Step 6: Train and Educate Employees
One of the most critical aspects of a successful cybersecurity strategy is employee awareness and training. Offer regular training sessions to educate your staff about the latest threats, best practices for online safety, and your company’s security policies.
Encourage a culture of vigilance, and empower employees to report any suspicious activities or incidents. Social engineering, such as phishing attacks, rely on the haste and unawareness of employees, so look at wider company practices as well.
Step 7: Establish an Incident Response Plan
Even with the best security measures in place, cyber incidents can still occur. Having an incident response plan ready will help you minimize the impact of a breach and recover more quickly. This plan should outline the steps to take in the event of a cyber attack, including:
- Identifying the affected systems
- Containing the incident
- Assessing the damage
- Communicating with stakeholders
- Restoring systems and data
- Learning from the incident and improving data protection
Step 8: Monitor and Review Your Strategy
Your cybersecurity strategy should be a living document that evolves as your business grows and the threat landscape changes. Regularly review and update your security and risk management plans to ensure they remain effective in protecting your organization from new and emerging threats.
This might involve performing regular security audits, penetration testing, and revising your policies as needed.
|
More cybersecurity reading you might like: |
Develop an Effective Cyber Security Strategy and Implementation Plan With Help From Experts
Effective information security without burdening workflows…that’s why businesses have trusted us for over 18 years. Work with seasoned cybersecurity professionals to deploy proven cybersecurity technologies across your organization.
Find out how we help organizations like yours implement IT security plans seamlessly and successfully defend against threat actors.