Business emails often contain sensitive data about clients or staff. Although internal email accounts are relatively secure compared to consumer options, implementing additional email security for small businesses remains necessary.
| “Poor email security is like bailing water out of the boat without plugging the leak. It is a must to address and one of the most frequent ways organizations are compromised for theft and cyber vandalism.” – Charles Bender, CEO, Attentus Technologies |
Plus, with email being the starting point for 91% of cyber attacks, these accounts truly are your organization’s biggest targets. That’s why today’s article will examine small business email security threats and best practices to avoid them.
Email Threats You Need to Protect Your Business From
Spear Phishing
Spear phishing is a more targeted form of phishing. It involves sending emails to specific individuals while posing as a trusted sender. These suspicious emails include personalized information that could only seemingly be known by the supposed sender. This personalization makes the deceptive emails more convincing.
While only 0.1% of all phishing emails sent involve spear phishing, it is successful 66% of the time. For that reason, it is particularly dangerous.
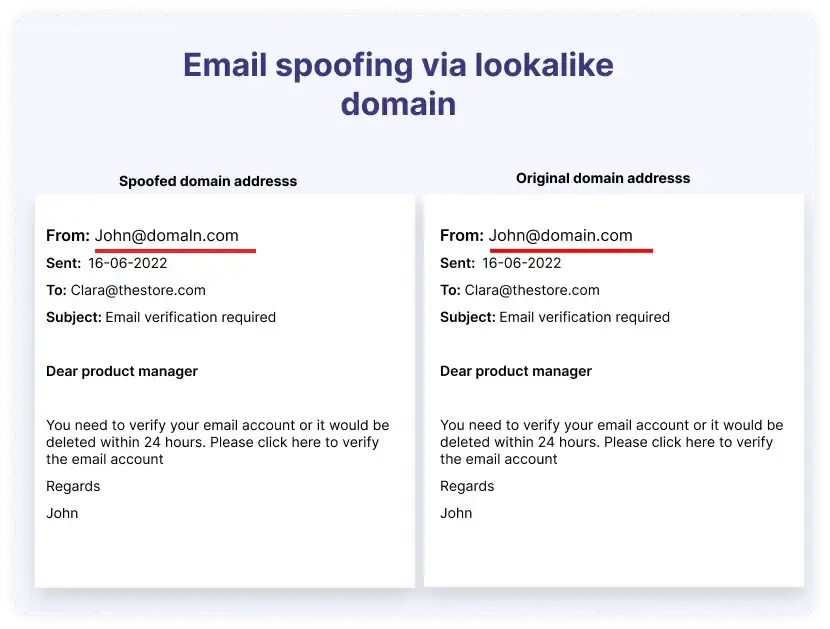
Spoofing
Spoofing refers to disguising communication from an unknown source as being from a trusted source.
This usually means forging the sender’s address to make it appear that the email is from a domain you trust. Senders may also make the domain address very close to a trusted address with the hope that the recipient won’t look closely enough to notice.
For example, take a look at these two email addresses.
Man-in-the-Middle Attacks
Man-in-the-Middle Attacks (MITM) involve an attacker secretly relaying and possibly altering the communication between two parties who believe they are directly communicating with each other. In the context of email, a MITM attack could mean the attacker intercepts an email, modifies its content, and then forwards it on to the recipient.
Business Email Compromise (BEC)
In BEC scams, attackers pose as company executives or trusted vendors by stealing their account access. These precisely targeted emails often request transfers of funds or confidential data, which can result in significant financial losses.
Data Exfiltration
Data exfiltration refers to the unauthorized transfer of data from a computer or other device. For example, hackers can compromise an email account and set up automatic forwarding rules to send incoming emails containing sensitive information to an external account.
Email Bombing
This occurs when an attacker sends a massive volume of emails to a single email address or system in a very short period. This attack overwhelms the email server or the recipient’s email account. The primary goal is to render the email service slow or unavailable for legitimate users. It may be used to distract from other malicious activities.
Learn More About How You Can Elevate Your Threat Protection: |
Email Security for Small Businesses: Best Practices
Enable Multi-Factor Authentication (MFA)
Multi-factor authentication significantly reduces the risk of email account breaches. This method requires users to provide two forms of identification before accessing their accounts. Small businesses can use authentication apps or hardware tokens as the second factor.
Enforce Strong Passwords
Despite how common password policies are, a surprisingly high number of users still use weak password practices. For instance, 59% of American adults use birthdays or personal names as their passwords, which is easily findable information. Educate your staff on what a strong password really means.
Avoid Public Wi-Fi
According to CloudSeureTech, 35% of professionals check their work emails on a mobile device. The problem with that practice is that there is a higher chance that they may use public Wi-Fi for this task. Discourage the practice or roll out a VPN for your staff. Public Wi-Fi is generally less secure and more susceptible to MITM attacks.
Get Expert Help Managing Your I.T. Infrastructure!Attentus Tech can be your new and improved I.T. department! |
Encrypt Emails
Implement end-to-end encryption (E2EE) for all email communications. This ensures that emails are encrypted from the moment they are sent until they are decrypted by the intended recipient. Plus, you should always encrypt sensitive attachments separately, even if the email message is encrypted.
Keep Email Software Up-to-Date
Keeping software and systems updated is a key practice in maintaining email security. Regular updates patch security vulnerabilities and enhance the software’s overall security features. Consider automating your update processes to ensure you don’t miss critical security patches.
Use Secure Email Gateways
Deploy secure email gateways that filter incoming and outgoing emails to detect threats and block data leaks. These gateways can be configured to identify and quarantine emails containing suspicious content or attachments.
Looking For Cybersecurity Services in The Pacific Northwest? |
|||
| Bellevue | Renton | Seattle | |
Get an Extra Hand With Your Email Security Solutions From Attentus
Maintaining email security software and revising practices can get time-consuming. As a busy business owner, you may not want to take precious hours from your work day for these tasks. It gets more complicated if you don’t have the in-house resources to do it all.
Thankfully, you can rely on Attentus Technologies to enhance your small business email security. We offer sophisticated cybersecurity tactics and will happily monitor your network 24/7 and spring into action if we see something suspicious.
Reach out today to get started.


